If you ignored FBI advice to reboot your router, don’t. It’s already a massive problem.

There’s no other way to say it: Walk over to your cable or DSL router right now, and disconnect the power. When it comes back on, you’ve done a good thing for the world — and you and your coworkers, for that matter.
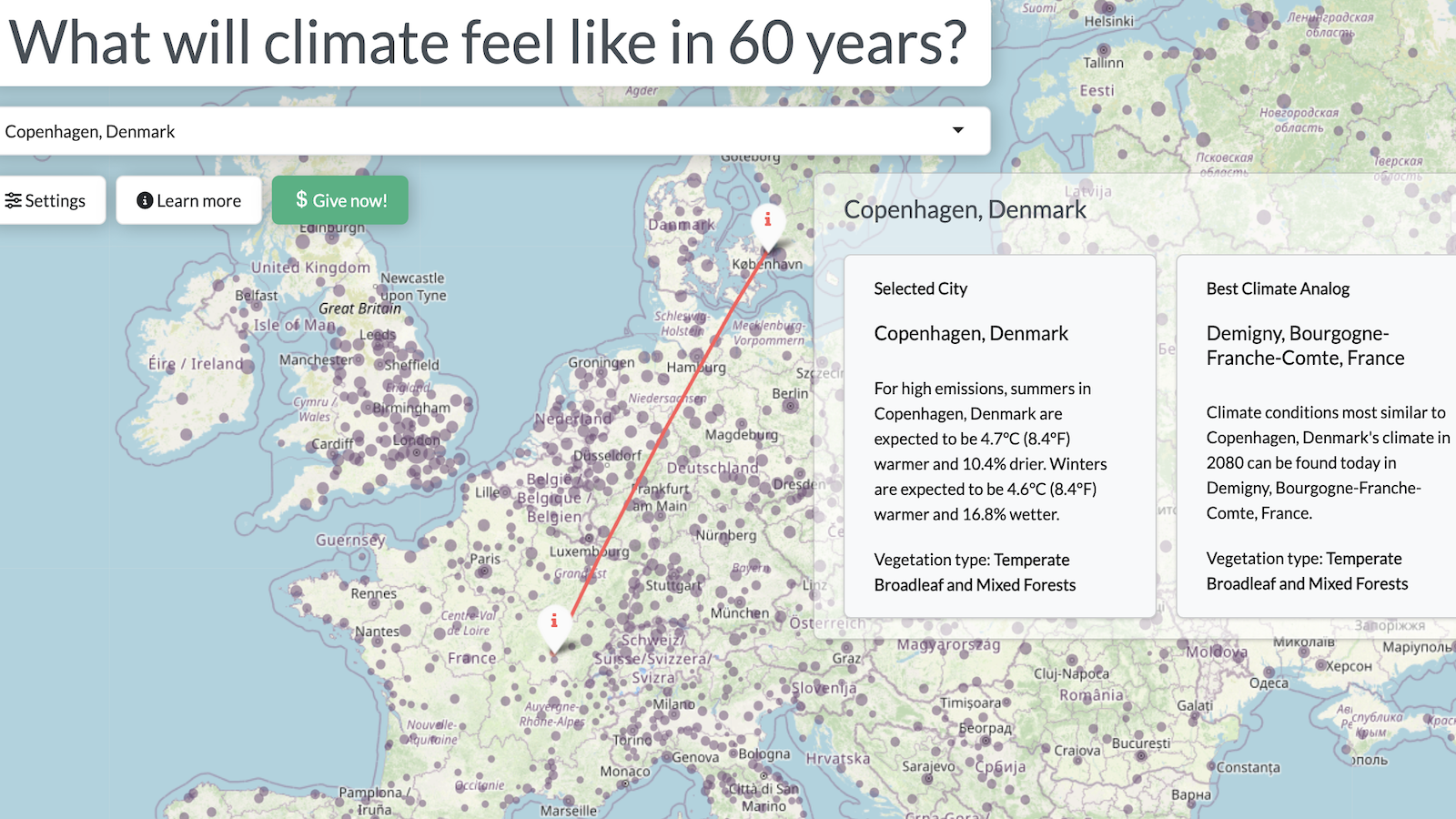
According to the FBI, foreign “cyber criminals” have compromised over 500,000 network routers in homes and small offices around the world. And they’re asking everyone who uses a router to connect to the Internet (basically, everyone except those who are hard-wired and those using a smart phone) to reboot. Now.
What they’re using is something called “VPNFilter” and it’s a particularly insidious infection that, according to the FBI, can “ … perform multiple functions, including possible information collection, device exploitation, and blocking network traffic.”
The motives of these hackers are not yet clear, but security company Talos has indicated it can collect files, data such a credit card info and other personal information that you’d typically type into a browser or tablet, and more. It has at least 3 stages, and likely more that haven’t been discovered yet. Each requires the previous stage to be in place in order to function, and as of right now, stage 2 and higher are short-circuited by a reboot of the device.

Image by Talos.
“The size and scope of the infrastructure by VPNFilter malware is significant,” the FBI added. It also states that the malware can render your device inoperable, so we recommend you reset your router no matter its model.
Some of the most common devices affected are made by Linksys, MikroTik, Netgear, and TP-Link, but there are more.
Here are the routers affected, according to Tom’s Guide:
“Cisco Talos listed the definitively affected routers as the
- Linksys E1200, E2500 and WRVS4400N
- Netgear DGN2200, R6400, R7000, R8000, WNR1000 and WNR2000
- TP-Link TL-R600VPN SafeStream VPN router
- MicroTik Cloud Core routers, mainly used by enterprises, may be affected if they run versions 1016, 1036 or 1072 of the MicroTik RouterOS
Cisco Talos found that two QNAP networked-attached-storage (NAS) drives, the TS-251 and TS-439 Pro, were also affected by VPNFilter.”
But also according to Tom’s Guide, there may be a lot more models affected eventually.
While a true infection will require more technical knowledge to clean (by things like disabling remote management settings, changing passwords and replacing them with more secure ones, and upgrading router firmware) this reboot measure will at least temporarily disrupt the malware, and help identify devices that are compromised. (And a hint: all devices such as cable modems and network routers have a default password, usually “admin,” “password,” or other such easily-guessed words. Change that if you can.)
So what are you waiting for?
And here’s Marc Goodman with some scary possibilities that hackers will be taking on, if they’re not already: