Practical physics: How quantum uncertainty will make our communications secure

- Quantum entanglement isn’t just a theoretical concept; it can have powerful real-world applications.
- By utilizing the uncertainty of the quantum world, we can create a more secure and powerful quantum internet.
- Tests show that we can use quantum entanglement and teleportation to securely transfer banking data or protect video calls from hacking.
This is the second of a four-article series on how quantum entanglement is changing technology and how we understand the Universe around us. In the previous article, we discussed what quantum entanglement is and how physicists in the early 1900s developed the idea that nature is uncertain. In this article, we discuss how entanglement can transform how we can communicate.
Quantum entanglement has taught us that nature is weird. Nothing is certain on the quantum scale. We may not know the properties of particles, but this is not because our instruments aren’t good enough. It is because particles don’t even have definite properties until they are observed. Nature is uncertain, and this uncertainty is embedded in the very fabric of the Universe.
You may be thinking: This is all very interesting, but what does it have to do with me?
The fact is — a lot. Quantum entanglement is not mere theory. It has real-world implications in many areas. Today, we are going to discuss a very practical application: securing our communications. By utilizing the uncertainty inherent at the quantum scale, our communications can become faster and more secure, transforming the internet and how we do business.
Quantum necessity
Many of the forms of digital communication we use would be considered classical communications — everything from the internet to calls on cell phones. Classical communications consist of strings of 1s and 0s, each of which holds a “bit” of information.
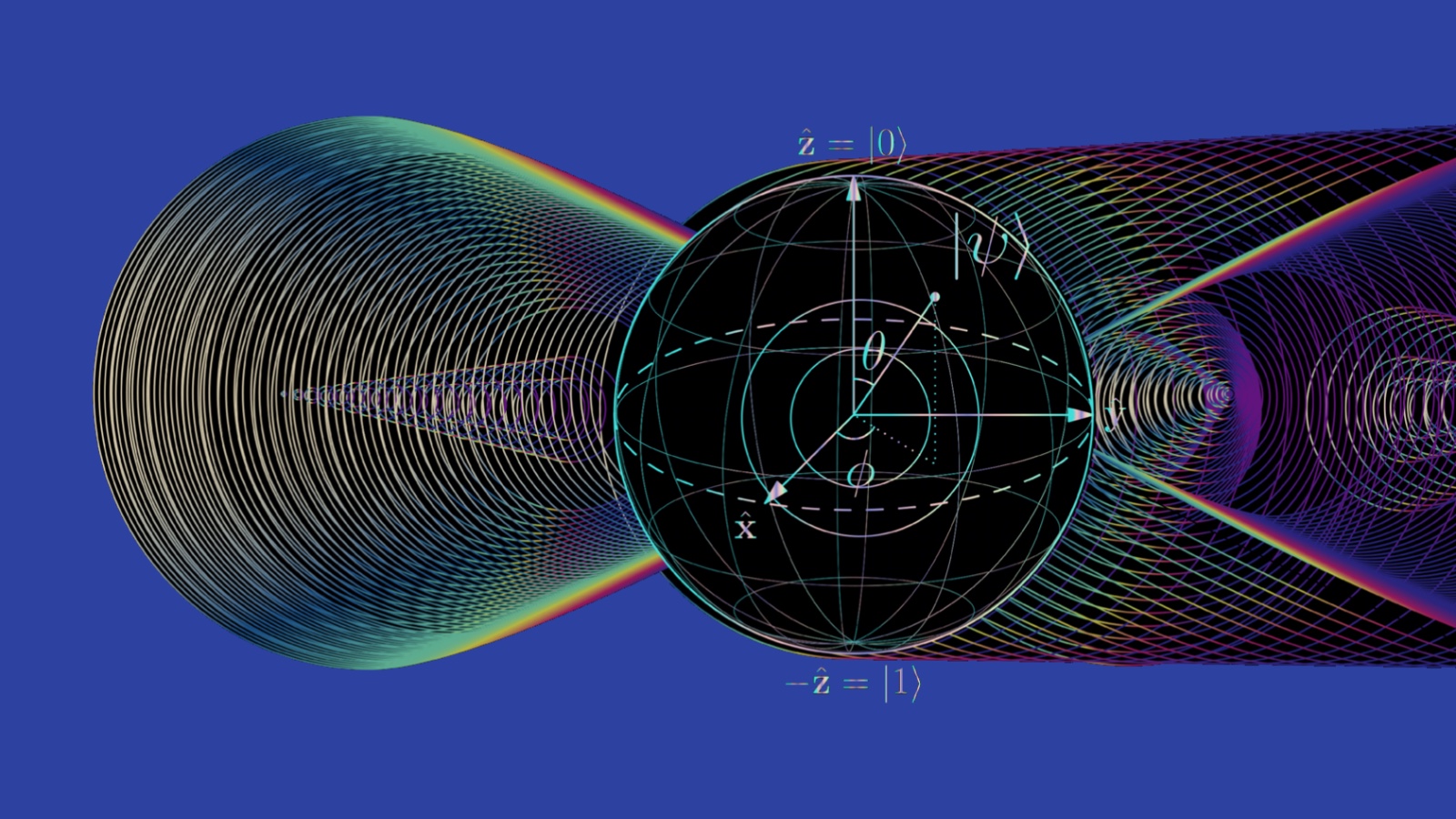
Quantum communications are different. Taking advantage of the uncertainty at quantum scales, we can let our information be both a 1 and 0 simultaneously. This bit of quantum information, or qubit, can be a superposition of states — a 1, 0, or a combination — until it is observed, at which point its wave function collapses. Because of superposition, qubits can perform more than one calculation at a time and hold more information than their classical bit counterparts.
Privacy in communication is not just nice to have; it is necessary. According to the Identity Theft Resource Center, there were 1,862 data breaches in 2021, compromising almost 300 million people. There are many sources of these data breaches. Many of them happen when information is transferred. Any communication over the internet is vulnerable to being intercepted and viewed by someone other than the intended recipient.
To protect our privacy, data that is transferred over classical communication channels can be encrypted. But the strength of this encryption is balanced by the ingenuity of the hacker. Classical communication relies on combinations of 1s and 0s. Hackers can look at those 1s and 0s, copy them, and send them on their way, with no one else being able to know that the message was intercepted. The level of security using quantum communication, on the other hand, is rooted in the laws of physics, and it could be made immune to hacking using a process called QKD, or quantum key distribution.
Let’s see one example of how this could work. Let’s say we have two people, Alice and Bob. Alice wants to send Bob some information. She employs two methods to transfer data. In the first, she sends encrypted classical data over a normal communication channel. To decrypt the data, Bob would receive a second piece of information from Alice – this time, a quantum message consisting of qubits transferred over a quantum channel. It might comprise photons with random polarization. This is Bob’s quantum key, and he can use it to decode the message. The idea is that the message should be understood only once the classical and quantum data are combined.
Using a quantum key has a few benefits over classical communications. The uncertain nature of the wave function keeps quantum information safe from eavesdropping, since that kind of interference would cause the qubits’ wave function to collapse. It is also not possible for a hacker to intercept, decrypt, and retransmit the signal. This is because an unknown quantum state cannot be copied. (This is referred to as the no-cloning theorem.) Therefore, if their signal is intercepted, both Alice and Bob will know.
Teleporting information
Things of course get more complicated in reality. A fraction of the quantum message will be destroyed in transit. For instance, a photon that is part of the message may interact with the edge of the fiber optic cable, causing its wave function to collapse. This process is called decoherence.
When Bob receives his key, he will compare it with Alice’s by sampling random qubits to see if it is similar enough. If the error rate is low, chances are that any errors are the result of decoherence, so Bob will go ahead and decode his message. If the error rate is high, someone may have intercepted the key. In this case, Alice will generate a new key.
While this is a lot more secure than classical communications, it is not perfect. The farther the quantum channel is, the higher the chance for decoherence. Therefore, the message can only travel a few tens of kilometers (in a fiber optic cable) before it becomes useless. Quantum repeaters can be used to help. They can decode the message and then re-encode it into a new quantum state, allowing it to travel farther.
However, each decoding gives hackers an opportunity to catch the message. The security of QKD also assumes that everything is operating flawlessly — and nothing in real life is flawless.
To increase security, we can turn to quantum entanglement and use a nifty method called quantum teleportation.
In this method, Alice and Bob both have an entangled qubit. Alice uses a third qubit, which she allows to interact with her qubit. As a result, Bob’s entangled qubit immediately takes the state of Alice’s qubit. Alice then sends the results of the interaction to Bob via a classical channel. Bob can use the results, combined with his qubit, to retrieve the message. This method is more secure because the actual message is not traveling between Alice and Bob — there is nothing to intercept.
The quantum communications race
Secure networks using QKD have been coming online and quickly growing. A team in the Netherlands first showed that they could transfer data 10 feet reliably using quantum teleportation in 2014. Three years later, a major quantum communication milestone was reached when a team of Chinese scientists used the Micius satellite to illustrate quantum entanglement over the longest distances yet achieved, between stations more than 1200 km apart.
Sizes of QKD networks have also grown swiftly. The first was created in Boston by DARPA in 2003. Currently, the largest QKD network is in China, spanning 4,600 km and consisting of optical cables and two ground-to-satellite links. Earlier this year, China launched Jinan 1 – a tiny quantum satellite weighing in at less than 100kg, designed to perform quantum key distribution experiments in low-earth orbit. Eventually, quantum communication may prove to be effective over vast distances in space.
Although the technology is still in an early phase, QKD networks have allowed for everything from secure banking data transfers to the world’s first quantum-encrypted video call between China and Vienna, Austria. As time goes on, quantum communications can offer huge benefits for sectors as wide-ranging as banking, security, and military. We are not at the point where quantum communications can be deployed to protect our internet communications, but we might not be far off.