Mystery unsolved: ghost ships circling off California
Credit: Courtesy of SkyTruth/Global Fishing Watch/Orbcomm/Spire
- ‘Circle spoofing’ is an as-yet unexplained version of GPS interference.
- It shows ships moving in virtual circles while they’re somewhere else.
- Is this the cheaper, off the shelf version of a well-known cyberweapon?

The Princess Janice, seen travelling from Point Reyes inland. Inset top right: moving around Utah, in circles. Inset bottom right: back home in Nigeria.Credit: Courtesy of SkyTruth/Global Fishing Watch/Orbcomm/Spire
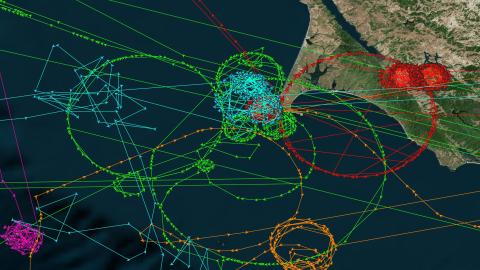
On June 5, 2019, the Nigerian crew boat Princess Janice made an impossible journey. Instead of ferrying crews to and from oil rigs in the Gulf of Guinea, it was somehow transported thousands of miles to the Pacific coast of northern California, just off Point Reyes. Even more amazingly, after a while it started to sail inland, ploughing across mountains and deserts all the way to Utah.
The Princess Janice was just one of a dozen ghost ships observed circling the seas off Point Reyes. And circling is the right word, as some ships seemed to ply the Pacific waters in mysteriously elliptical movements, at a constant speed of exactly 20 knots. Except that they didn’t. The Princess Janice never left its home waters. Nor did any of the other ships, which all continued to sail the seas off Equatorial Guinea, Malaysia, Norway, and other far-flung places.
It wasn’t the actual, physical ships that flew halfway across the globe, just their virtual positions, as reported by their AIS (1) transponders. Some ships were displaced for just a few hours, but the Princess Janice‘s virtual trip to North America lasted about two weeks. And not all hung around Point Reyes. Some showed up near Madrid or Hong Kong.

AIS tracks from five ships who ‘jumped’ to Point Reyes, from places all over the globe.Credit: Courtesy of SkyTruth/Global Fishing Watch/Orbcomm/Spire
The Point Reyes incident, publicized by Bjorn Bergman, a researcher for environmental watchdogs SkyTruth and Global Fishing Watch, was the latest example of a phenomenon known as ‘circle spoofing’, a refined and as yet unexplained cousin of GPS (2) spoofing. It is unclear what–or who–caused these circles, and why: malfunction or manipulation?
Now, messing with GPS signals is not new. It’s been part of the electronic warfare arsenal for decades. Russia, notably, has been singled out as a ‘pioneer’ in this area. A report by the Center for Advanced Defense Studies (C4ADS) in Washington DC claims the Russians have a mobile electronic warfare team that jams GPS signals whenever and wherever President Putin appears in public.
One step up from mere jamming is spoofing: tricking someone that a GPS-geolocated object is somewhere else than it actually is. The AIS transponders of ships seem particularly prone to this.
Russia has used GPS spoofing in a number of places, notably Crimea, Syria, and the Black Sea, says the C4ADS report. For example, in 2017, 20 ships in the Black Sea reported a position 32 km inland, near Gelendzhik Airport. It’s also been claimed Russia uses ‘spoofing’ to hide Putin’s now-infamous Black Sea palace, the existence of which was revealed by controversial dissident Alexei Navalny.

A world map of Russian GPS spoofing: not just in and near Russia, but also in Syria.Credit: Above us Only Stars – Exposing GPS Spoofing in Russia and Syria (C4ADS, 2019)
GPS spoofing has obvious strategic implications. Iran in particular has proved a quick student and seems to have learned to use spoofing to its advantage.
- In 2011, Iran claimed to have used GPS spoofing to trick a Lockheed Martin RQ-170 ‘Sentinel’ drone, operated by the CIA above Afghanistan, to land at an Iranian airfield. The capture helped Iran clone its own drone within a year.
- In 2016, Iran probably used GPS spoofing to lure two US Navy boats into Iranian territorial waters, where the Iranian Navy appeared to be ready and waiting for them.
- And in 2019, British intelligence warned merchant vessels in the Gulf that Iran might use GPS spoofing to lure them into Iranian waters, as a pretext to seizing them.
And then there’s one step up from GPS spoofing: circle spoofing. In ‘regular’ GPS spoofing, the location (typically of a ship) is ‘transported’ to a static point somewhere else. In circle spoofing, the location is moved to a dynamic position, rotating in a circular pattern. This makes circle spoofing more difficult to read, and potentially more dangerous – although the actual intention behind the phenomenon remains unclear.
Circle spoofing came to light after July 2019 (3).That’s when the American container ship MV Manukai, upon entering Shanghai harbor, experienced total failure of both its AIS transponder and its two GPS units. Just before all the alarms went off, its AIS display behaved in a very peculiar manner. It showed another ship approaching, disappearing, showing up docked, and then again moving towards the Manukai. All the while, a visual check confirmed, the other ship had been at dock.

When approaching the center of the disturbance, the AIS signature of the Chinese cargo ship Hua Hia Ji Hao (in yellow) jumps from the Huangpu River onto dry land. Red: positions of other vessels. Credit: Courtesy of SkyTruth/Global Fishing Watch/Orbcomm/Spire
The crew of the Manukai reported the incident stateside, where analysts discovered an epidemic of spoofing attacks in Shanghai harbor which had started the previous summer and culminated on the day the Manukai was attacked, just one of around 300 vessels that were being ‘spoofed’ that day.
It’s unclear who’s doing the spoofing. Could it be the Chinese government testing out cyberweapons? Or perhaps criminals trying to confound the authorities? Illegal sand dredgers and oil smugglers are desperate to use any means to evade capture. The latter option would explain why one particular patrol boat operated by the Maritime Safety Authority, Shanghai’s river police, was spoofed almost 400 times over a nine-month period.
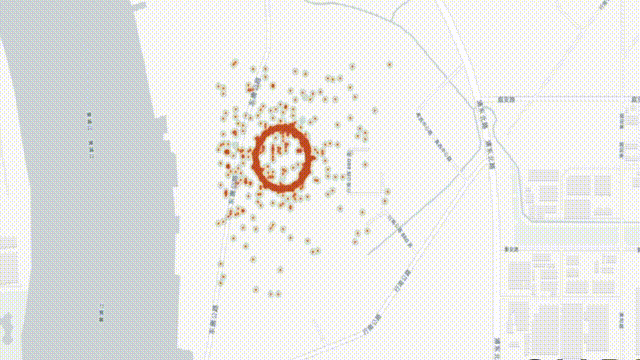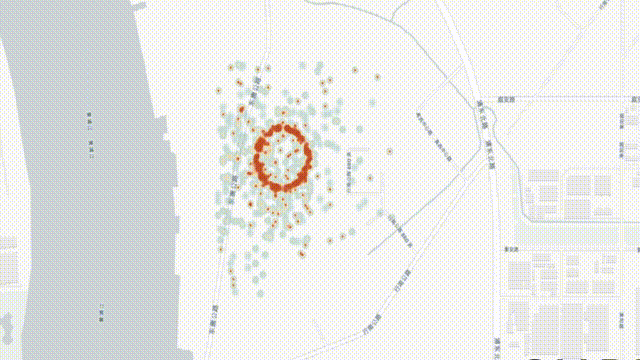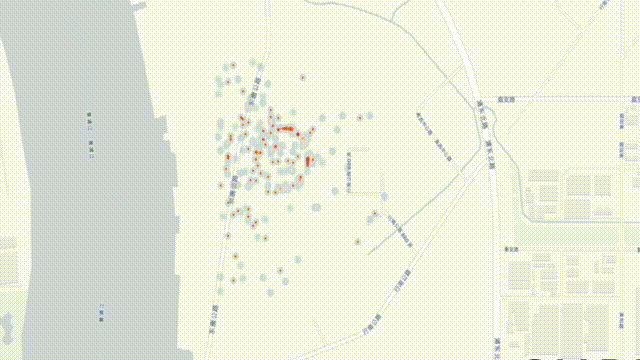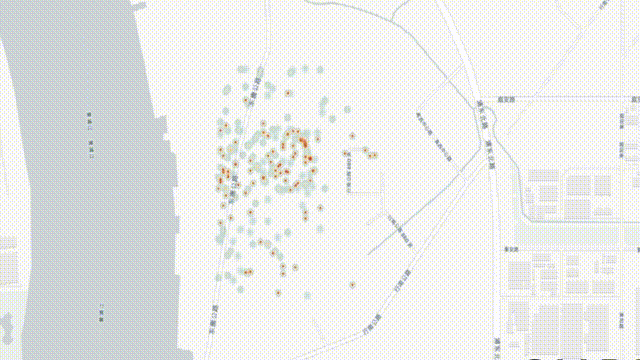
But what was even more remarkable than the sheer volume of the spoofing was its cartographic shape: the ships jumped from one location to another in a circular movement, centered on the eastern bank of the Huangpu River.
Why? How? Those questions have yet to be answered satisfactorily, but C4ADS found an ingenious way to discount the possibility that the ships’ AIS was somehow at fault. Analysts looked at anonymized location data provided by the Strava fitness app, used by a considerable number of Shanghai’s 10 million cyclists.

The eye of the storm: a spoof circle about 200 meters in diameter. Most positions on the ring move at 31 knots, much faster than normal vessel speed, and appear to be going counterclockwise.Credit: Courtesy of SkyTruth/Global Fishing Watch/Orbcomm/Spire
Turns out they too were apparently going in circles, when approaching the waterfront. This proved the spoofing attacks targeted all GPS devices, not just the ships’ AIS transponders.
But that still did not resolve the mystery of the circular spoofs, which were quickly dubbed ‘crop circles’ – an allusion to the mysterious figures that regularly appear in the grain fields of southern England.
Do the positions at which the circles are centered offer any clue? One such circle is positioned exactly around the Sinopec Shanghai Petrochemical Company. Does that suggest state involvement cloaked as private enterprise, or rather a rogue ‘commercial’ venture? Or are the circles themselves clever misdirections, activated by devices stationed elsewhere?
What does seem certain, is that circle spoofing is catching on. Following the incidents in Shanghai (involving vessels close by) and off Point Reyes (involving ships very far away), a report came in from Iran in March of 2020, where a GPS device was observed moving in a large circle in downtown Tehran (so nowhere near any coast), at a constant speed of 22 miles per hour.
Credit: Courtesy of C4ADS, MIT Review
The spoofing occurred near the AJA University of Command and Staff – the staff college for Iran’s Army, also known as the country’s ‘War University’. Again, a Strava heat map showed local athletes running (or cycling) in circles in that same area, apparently oblivious to local roads and buildings.
Meanwhile, the mysteries of circle spoofing–who is doing it, how and why–have yet to be cracked. Reports of circle spoofing near various oil terminals in China suggests that it may be a way to defend these installations from attack – in fact, a Saudi oil facility suffered major damage in an attack by an unidentified drone (rumored to be Iranian in origin) in 2019.
Another theory is that circle spoofing could be a sign that GPS spoofing, once so complex and expensive that it must have required state involvement, has now been ‘commoditised’: it can now be used by low-power, short-range devices that can target single ships instead of having to cover a wider area.
And that’s a scary thought: it could open up maritime traffic to a whole new kind of piracy – spoofing luxury yachts or ships with valuable cargo right into the lair of the 21st-century disciples of Long John Silver, armed with keyboards instead of cutlasses.
Many thanks to Dana Goward (President, Resilient Navigation & Timing Foundation), Bjorn Bergman (Project Manager, SkyTruth; analyst, Global Fishing Watch) and Thomas Ewing (Chief of Analysis, C4ADS).
For more information, see:
- GPS Jamming and Spoofing Reported at Port of Shanghai (The Maritime Executive, 13 August 2019)
- Ghost ships, crop circles and soft gold (MIT Review, 15 November 2019)
- Systematic GPS Manipulation Occurring at Chinese Oil Terminals and Government Installations (SkyTruth, 12 December 2019)
- AIS Ship Tracking Data Shows False Vessel Tracks Circling Above Point Reyes, Near San Francisco (SkyTruth, 26 May 2020)
Strange Maps #1074
Got a strange map? Let me know at strangemaps@gmail.com.
Follow Strange Maps on Twitter and on Facebook.
(1) AIS stands for Automatic Identification System, which supplements radar as a means to avoid collisions and determine locations of ships. It uses GPS (or similar positioning systems) to transmit information on a ship’s identity, position and movements to nearby ships and monitoring facilities in a range of 10-20 nautical miles. Mandatory for most seafaring vessels, AIS is fitted on around 300,000 passenger and cargo ships worldwide.
(2) GPS is short for Global Positioning System. It’s a system for radio navigation based on a network of (currently 31) US satellites, operated by the US Space Force. The network sends exact geolocation and time information to any GPS receiver on earth (if within an unobstructed line of sight of at least four GPS satellites). Started in the 1970s as a military project, it was opened for civilian use in the 1980s. In 2000, restrictions were lifted, allowing accuracy to within 5 meters.
(3) The Point Reyes incidents were discovered later.